A glossary of my computing terms
Mazdak Allayari
Published : 25/08/2005
Last update : 01/01/2022
Internet
Organization
Regional
Internet Registries
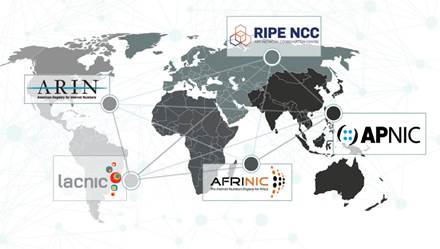
There
are five Regional Internet Registries (RIRs) in the world. RIRs manage,
distribute, and register Internet number resources (IPv4 and IPv6 address space
and Autonomous System (AS) Numbers) within their respective regions.
RIR
Operation, Oversight and Stability
Each RIR
operates as a not-for-profit, member-based association in its respective region
in accordance with the laws of the country in which it is located. RIRs
distribute Internet number resources according to the policies developed by
their respective regional community using established open, inclusive and
bottom-up Policy Development Processes (PDP).
Member-elected
boards govern each RIR. Boards provide fiduciary oversight, strategic guidance,
and verification of the policy development process. RIRs have also implemented
mechanisms to avoid capture through election processes, Bylaws, articles of
incorporation, and membership provisions. A Joint RIR Stability Fund also
exists to ensure that the global RIR system remains robust. Find out more.
The NRO
The
Number Resource Organization (NRO) was established in 2003 as a coordinating
body for the five Regional Internet Registries (RIRs) to act on matters of
global importance to all five RIRs, to participate in global Internet
governance activities and to coordinate joint projects across the global RIR
system. Find out more.
The Role
of Regional Internet Registries
Within
their respective regions, RIRs provide services to administer, manage,
distribute and register Internet number resources, mainly to their members.
The global
RIR system ensures that each Internet number resource is uniquely assigned to
one party to ensure smooth functioning of the Internet, and that they are
distributed based on justified need. How the RIRs distribute Internet number
resources within their regions is defined by the policies that each RIR’s
community develops using its own PDP.
RIR
Members
RIR
members are comprised of Internet service providers (ISPs), governments,
universities, civil society, end users, for-profit and not-for-profit
enterprises of all sizes and across all business sectors.
Members
pay fees to an RIR based on the type and amount of services they require. Each
RIR sets its own membership requirements and fees.
RIR
membership information: AFRINIC | APNIC |
ARIN | LACNIC | RIPE NCC
RIR
Communities
RIR
communities consist of anyone who is interested in Internet number resources
and the policies governing how they are distributed. RIR community participants
are not required to be a member of any RIR. Anyone can join the discussion and
everyone has an equal voice.
Community
participants can also take part in other Internet governance activities that
are directly related to Internet number resource management, such as the
Address Supporting Organization Address Council (ASO AC).
Open and
Transparent
Discussions
on public mailings lists are an important part of the policy-making process.
Each RIR maintains policy discussion mailing lists, which are open to all and
are publicly archived.
RIR
policy development mailing lists: AFRINIC | APNIC | ARIN | LACNIC | RIPE NCC
RIR
Meetings
Policy
discussions also take place during RIR meetings, which are open for everyone to
participate in, both on-site or via remote participation online. Each RIR holds
around two meetings a year. In addition to discussions on Internet number
resource policy, the meetings also include technical presentations, training
courses and workshops. The NRO itself does not hold any meetings.
Upcoming
RIR Meetings: AFRINIC | APNIC |
ARIN | LACNIC | RIPE NCC
Regional
Policy Development Process
RIR
policy development processes (PDP) are designed so anyone who is interested in
Internet number resource policy can participate. Anyone can propose a policy or
an amendment to a current policy. Once a policy proposal is submitted, anyone
can submit comments, or provide support or objection to the proposal. The
community then accepts or rejects the proposal by consensus. While each
RIR’s PDP is tailored to local requirements, they are all open,
transparent and bottom-up. Find out more.
Global
Policy Development
Global
policies govern how Public Technical Identifiers (PTI), the organization
charged with performing the IANA functions, issues Internet number resources to
the RIRs. A global policy proposal can be submitted by anyone. For it to be
accepted, the same version of the proposal must be considered in all five RIR
regions and subsequently accepted according to each community’s policy
development process before being ratified. Find out more.
Internet
Organisations in brief description
The Internet is a collection of autonomous and
interconnected networks that implement open protocols and standards. No
single person, government or organisation owns or
controls the Internet or the World Wide Web. There are, however, a number
of organisations and bodies – both
international and national – which regulate, monitor, make
recommendations or set guidelines covering issues such as infrastructure,
domain registration, web technologies, content and accessibility.
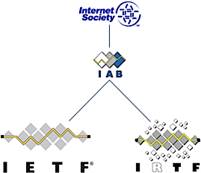
A non-profit organization called ISOC (Internet Society)
has some control over the future of the Internet. It appoints a technical
advisory group called the IAB (Internet Architecture Board)
to evaluate and set standards.
Input on protocols and standards can come from anybody –
individuals, research groups, companies and universities. A specification
is submitted as an Internet draft and made available for review and comments.
Various Internet organizations evaluate whether these specifications
should be advanced – through a process that may elevate the specification
through different levels until it potentially reaches a ‘standards’
status.
In general, the IETF (Internet Engineering Task Force)
forms working groups to develop specifications, which are evaluated by the IESG (Internet Engineering Steering Group)
in conjunction with the IAB. ISOC then
publicizes the new standards. Web standards are promulgated by the W3C (World Wide Web Consortium)
and other groups.
Activity – Internet Organisations – Introductory Research
W3C (World Wide Web Consortium)
W3C develops interoperable technologies (specifications,
guidelines, software and tools) for the Web. Its goal is to lead the
World Wide Web to its full potential by developing protocols and guidelines
that ensure long-term growth for the Web.
The W3C is an international industry consortium founded in October
1994 to develop common protocols that promote the evolution of the World Wide
Web and ensure its interoperability.
Services provided by the Consortium include: a repository of
information about the World Wide Web for developers and users; reference code
implementations to embody and promote standards; and various prototype and
sample applications to demonstrate use of new technology.
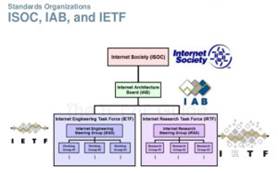
IETF (Internet Engineering Task Force)
The IETF is a large open international community of network
designers, operators, vendors and researchers concerned with the evolution of
the Internet architecture and the smooth operation of the Internet. The
actual technical work of the IETF is done in its working groups which include
Applications, Internet, Network Management, Operational Requirements, Routing,
Security, Transport and User Services. Working groups are managed by
members of the IESG. The IAB provides architectural oversight. The
IETF also facilitates technology transfers from the IRTF to the wider Internet
community. It is open to any interested individual.
ISOC (Internet Society)
The ISOC is an international organization which promotes global
cooperation and coordination for the Internet and its internetworking
technologies and applications. ISOC approves appointments to the IAB from
nominees submitted by the IETF Nominating Committee. ISOC membership is open to
any interested person
IAB (Internet Architecture Board)
The IAB is a technical advisory group of the ISOC (Internet
Society). Its responsibilities are to appoint a new IETF chair and IESG
candidates, serve as an appeal board, manage editorial content and publication
(RFCs) and provide services to the Internet Society.
IESG (Internet Engineering Steering Group)
The IESG is chartered by ISOC to provide technical management of
IETF activities and the Internet standards process. The IESG manages the
IETF working groups and is directly responsible for the actions associated with
entry into and movement along the Internet ‘standards track’
including final approval of specifications as Internet standards.
IRTF (Internet Research Task Force)
The purpose of the IRTF is to promote research of importance to
the evolution of the future Internet by creating focused, long-term and small
research groups working on topics related to Internet protocols, applications,
architecture and technology. Participation is by individual contributors
rather than by representatives of organizations. The IRSG manages the
research groups and holds workshops that focus on the evolution of the Internet
and discuss research priorities from an Internet perspective.
W3C (World Wide Web Consortium) – Web Accessibility
Initiative
WAI develops –
guidelines which are widely regarded as the international standard for Web
accessibility and support materials to help understand and implement Web
accessibility through international collaboration.
Web Standards Project
The Web Standards Project persuades vendors to follow standards to
ensure accessibility for all.
 ICANN (Internet Corporation for Assigned Names and Numbers)
ICANN (Internet Corporation for Assigned Names and Numbers)
The Internet Corporation for Assigned Names and Numbers (ICANN) is
an internationally organized, non-profit corporation formed in September 1998
that has responsibility for Internet Protocol (IP) address space allocation,
protocol identifier assignment, generic (gTLD) and country code (ccTLD)
Top-Level Domain name system management and root server system management
functions.
IANA (Internet Assigned Numbers Authority)
The IANA is the authority originally responsible for the oversight
of IP address allocation, the coordination of the assignment of protocol
parameters provided for in Internet technical standards, and the management of
the DNS, including the delegation of top-level domains and oversight of the
root name server system.
 InterNIC (Internet Network Information Center)
InterNIC (Internet Network Information Center)
--------End Of Internet
Organisation ------------------------
Laws about
data protection
General Data Protection
Regulation (gdpr.eu)
The General Data
Protection Regulation (GDPR) is the toughest privacy and security law in the
world. Though it was drafted and passed by the European Union (EU), it imposes
obligations onto organizations anywhere, so long as they target or collect data
related to people in the EU. The regulation was put into effect on May 25,
2018. The GDPR will levy harsh fines against those who violate its privacy and
security standards, with penalties reaching into the tens of millions of euros.
With the GDPR, Europe
is signaling its firm stance on data privacy and
security at a time when more people are entrusting their personal data with
cloud services and breaches are a daily occurrence. The regulation itself is
large, far-reaching, and fairly light on specifics, making GDPR compliance a
daunting prospect, particularly for small and medium-sized enterprises (SMEs).
We created this website
to serve as a resource for SME owners and managers to address specific
challenges they may face. While it is not a substitute for legal advice, it may
help you to understand where to focus your GDPR compliance efforts. We also offer
tips on privacy tools and how to mitigate risks. As the GDPR continues to be
interpreted, we’ll keep you up to date on evolving best practices.
If you’ve found
this page — “what is the GDPR?” — chances are
you’re looking for a crash course. Maybe you haven’t even found the
document itself yet (tip: here’s the full regulation). Maybe you
don’t have time to read the whole thing. This page is for you. In this
article, we try to demystify the GDPR and, we hope, make it less overwhelming
for SMEs concerned about GDPR compliance.
APIPA
Automatic Private Internet Protocol Addressing, in
absent of DHCP this is an auto attribute address.
NAT
Every
TCP/IP packet contains a source IP address, source port, destination IP address
and destination port. All types of NAT create NAT mappings using these values.
For example a connection from an internal client with IP 192.168.0.1 using port
56876 may go to a website IP 56.45.78.89 (destination IP address) on port 80
(destination port) using IP of 45.34.78.98 (translated source IP) and port
56876 (source port). NAT creates a mapping using these 4 values to the
192.168.0.1 internal client for that specific connection. When packets come
back from the website to the router using the same values associated with that
mapping NAT forwards the packets to the internal client.
Dont confuse
NAT restriction with NAT translation – For example a Ful Cone NAT only
looks at the destination port when choosing whether to accept the connection or
not (the restriction). When it does the actual the NAT translation however, it
always uses the 4 values mentioned above.
There
are four types of NAT as follows:
Full
Cone NAT (Static NAT)
A full
cone NAT (also known as a one to one NAT) is the only type of NAT where the
port is permanently open and allows inbound connections from any external host.
A full cone NAT maps a public IP address and port to a LAN IP and port. Any
external host can send data to the LAN IP through the mapped NAT IP and port.
If it tries to send data through a different port it will fail. This type of
NAT is also known as port forwarding. This is the least restrictive type of
NAT; the only requirement is that the connection comes in on a specific port
(the one you opened).
Example
- My PC has a website running on
port 80. I create a one-to-one rule that maps the router WAN IP of 81.45.87.98
to 192.168.0.1 with port 80 to port 80. Any external host that sends data to
81.45.87.98 on port 80 is NATed (and sent) to 192.168.0.1 port 80.
Note:
the port numbers do not have to be the same; I could run my website on port
56456 but create the NAT mapping to forward port 80 to port 56456. This gives
the appearance to the public Internet that my website is on port 80. A
connection attempt on any other port is dropped.
Restricted
Cone NAT (Dynamic NAT)
A
restricted cone NAT works in the same way as a full cone NAT but applies
additional restrictions based on an IP address. The internal client must first
have sent packets to IP address (X) before it can receive packets from X. In
terms of restrictions the only requirement is that packets come in on the
mapped port and from an IP address that the internal client has sent packets
to.
Example
- My PC makes an outbound
connection to a website (56.45.34.78) with my source IP 192.168.0.1 and source
port 56723. The NAT creates a (dynamic) mapping to my PC using source port
56723. Packets that arrive with a source IP of 56.45.34.78 (the website IP)
using a destination port of 56723 (which was the outbound NATed source port)
will be accepted and sent to my PC. Connection attempts from any other IP using
the correct port of 56723 will be dropped. Connection attempts from the correct
IP with a destination port other than 56723 will also be dropped.
Port
Restricted Cone NAT (Dynamic NAT)
A port
restricted cone NAT acts in exactly the same way as a restricted cone NAT but
applies restrictions to ports also. Where a restricted cone NAT will accept
connections from any source port a port restricted cone NAT restricts this
further by only accepting connections from the IP address and port it sent the
outbound request to.
Example
- My PC makes an outbound
connection to website IP 217.87.69.8 on port 80 (destination port). The NAT
maps my source IP 192.168.0.1 to the WAN IP of 81.45.87.98 and source port
56723. When the website sends packets back it must have it’s
source IP as 217.87.69.8, destination port as 56723 (like a restricted cone
NAT) but in addition the source
port must be 80. If any of these three are different a port restricted cone NAT
drops the connection.
Symmetric
NAT (Dynamic NAT)
A
symmetric NAT applies restrictions exactly the same way as a port restricted
cone NAT but handles the NAT translation differently. Symmetric NAT is more
complicated and has it’s own unique problem so
I have wrote a separate article dedicated to Symmetric NAT and It’s
Problems.
DNAT
Destination
network address translation (DNAT) is a technique for transparently changing
the destination IP address of an end route packet and performing the inverse
function for any replies. Any router situated between two endpoints can perform
this transformation of the packet.
DNAT
is
commonly used to publish a service located in a private network on a publicly
accessible IP address. This use of DNAT is also called port forwarding, or DMZ
when used on an entire server, which becomes exposed to the WAN, becoming
analogous to an undefended military demilitarized zone (DMZ).
SNAT
The
meaning of the term SNAT varies by vendor. Many vendors have proprietary
definitions for SNAT:
source NAT is the common
expansion, as the counterpart of destination NAT (DNAT)
stateful NAT is used by
Cisco Systems
static NAT is used by
WatchGuard
secure NAT is used by F5
Networks and by Microsoft (in regard to the ISA Server)
IKE2
The Internet Key Exchange version 2 (IKEv2) Protocol dynamically establishes and maintains a shared state between the end-points of an IP datagram. IKEv2 performs mutual authentication between two parties and establishes the IKEv2 Security Association (SA). The IKE-SA uses shared secret information that it stores to do two different functions:
1. Establish CHILD-SAs for Encapsulated Security Payload (ESP) Protocol and/or Authentication Header (AH) Protocol
2. Defines the cryptographic algorithms to be used by the SAs
IKEv2 is a request/response pair protocol. These pairs are referred to as exchanges. The requester bears the burden of ensuring reliability. If a response is not received the requester can either retransmit or abandon the connection. IKEv2 has four types of exchanges:
1. IKE_SA_INIT- This is the first exchange that establishes the IKE-SA and MUST complete before any further exchanges can happen. It performs three functions in the setup of the IKE-SA.
o Negotiates security parameters for the IKE-SA
o Sends nonces
o Sends Diffie-Hellman values
2. IKE_AUTH- This is the second exchange and MUST complete before any further exchanges can happen. It performs three required functions:
o Transmits identities
o Proves knowledge of the secrets related to those identities
o Establishes the first, and usually the only, AH and/or ESP CHILD-SA
3. CREATE_CHILD_SA – This is simply used to create additional CHILD-SAs as needed
4. INFORMATIONAL- This is a maintenance exchange that performs a variety of functions to maintain the SAs. Some of these function include:
o Delete SAs as needed
o Report error conditions
o Check SA liveliness
o Other SA housekeeping functions
Once the first two mandatory exchanges have completed in their proper order, all subsequent exchanges can happen in any order necessary. In some cases there will be no future exchanges once everything is setup. An example IKEv2 exchange is shown in
Figure1

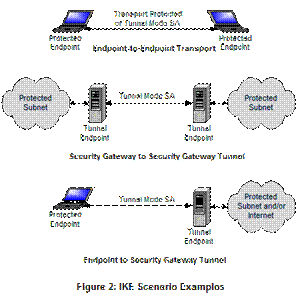
IKEv2 is expected to operate in a variety of scenarios; examples of three scenarios can be seen in Figure 2. The Endpoint to Endpoint Transport scenario (upper diagram) shows both the endpoints implementing IPsec. This scenario can use either transport or tunnel mode. The middle diagram shows Security Gateway to Security Gateway Tunnel scenario. This is a case where the endpoints do not implement IPsec but nodes between the endpoints do. This implementation is completely transparent to the users. The last diagram shows an example of Endpoint to Security Gateway Tunnel scenario where a endpoint implementing IPsec connects to a Security Gateway to securely access the network on the other side. Others scenarios are possible and can include a combination of the three shown.

IKEv2 employs a number of cryptographic protocols to accomplish all the security requirements of Key Management. IKEv2 is based on the Diffie-Hellman (DH) Key Management Protocol. IKE has four transform types that are mandatory to implement:
1. Encryptions
Algorithmes – Common algorithmes
DES,
3DES,
RC5, IDEA, 3IDEA,
CAST,
BLOWFISH, and
AES
2. Pseudo-Random Functions –
Common functions
HMAC and
AES
3. Integrity Algorithms – Common
Algorithms
HMAC,
DES,
KPDK, and
AES
AH (IP Authentication Header), RFC
4302
The IP Authentication
Header (AH) is used to provide connectionless integrity and data origin
authentication for IP datagrams (hereafter referred to as just
"integrity") and to provide protection against replays. This latter,
optional service may be selected, by the receiver, when a Security Association (SA) is established. (The
protocol default requires the sender to increment the sequence number used for anti-replay,
but the service is effective only if the receiver checks the sequence number.)
However, to make use of the Extended Sequence Number feature in an
interoperable fashion, AH does impose a requirement on SA management protocols
to be able to negotiate this new feature.
AH
provides authentication for as much of the IP header as possible, as well as
for next level protocol data. However, some IP header fields may change in
transit and the value of these fields, when the packet arrives at the receiver,
may not be predictable by the sender. The values of such fields cannot be
protected by AH. Thus, the protection provided to the IP header by AH is
piecemeal.
AH may
be applied alone, in combination with the IP Encapsulating
Security Payload (ESP), or in a nested fashion. Security services can be
provided between a pair of communicating hosts, between a pair of communicating
security gateways, or between a security gateway and a host. ESP may be used to
provide the same anti-replay and similar integrity services, and it also
provides a confidentiality (encryption) service. The primary difference between
the integrity provided by ESP and AH is the extent of the coverage.
Specifically, ESP does not protect any IP header fields unless those fields are
encapsulated by ESP (e.g., via use of tunnel mode).
Encapsulating Security Payload (ESP),
RFC 4303
The ESP header is designed to provide a mix of security services in IPv4 and IPv6. ESP may be applied alone, in combination with AH, or in a nested fashion.
Security services can be provided between a pair of communicating hosts, between a pair of communicating security gateways, or between a security gateway and a host. The ESP header is inserted after the IP header and before the next layer protocol header (transport mode) or before an encapsulated IP header (tunnel mode). ESP can be used to provide confidentiality, data origin authentication, connectionless integrity, an anti-replay service (a form of partial sequence integrity), and (limited) traffic flow confidentiality. The set of services provided depends on options selected at the time of Security Association (SA) establishment and on the location of the implementation in a network topology.
SWITCHING
Switching
operates at
-Layer
2 of the OSI model, where packets are sent to a specific switch port based
on destination MAC addresses.
Devices
in the same layer 2 segment do not need routing to reach local peers. What is
needed however is the destination MAC address which can be resolved through the
Address Resolution Protocol (ARP).
Routing
operates at
-Layer
3, where packets are sent to a specific next-hop IP address, based on
destination IP address.
Switch
Core (Layer 3) must active
A
protection against DDoS,
A Fault
tolerance for High availability,
Fault tolerance
in switching by two protocols
HSRP (Cisco’s Hot Standby Routing Protocol),
VRRP (Virtual Router Redundancy Protocol), [protocol is described in Internet Engineering Task Force (IETF) publication RFC 5798]
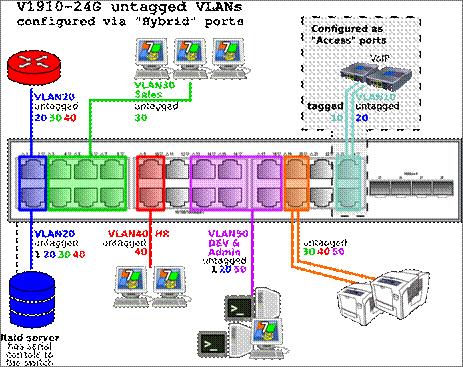
TAGGING
Differences
Between HP VLAN tagging and Cisco VLAN Terminology
HP VLAN
Tagging Terminology Differences Defined
VLAN
Modes
HP Procurve switches have four VLAN modes;
"Untagged", "Tagged", "No", and
"Forbid". Untagged mode is the equivalent of Access Mode in Cisco IOS
terminology, which is used for end points, or devices not passing VLAN traffic
forward (such as client ports; desktops, printers, etc.). Tagged mode is the
same as Trunk mode in Cisco, which is used for ports that connect devices and
are passing traffic forward (uplink or downlink ports on a switch or router).
No mode means the physical port is not a part of the VLAN. Forbid mode
restricts the port you added from communicating with that VLAN, regardless of
any other tag setting.
Trunk
The term
Trunk means two different things when dealing with HP or Cisco equipment, so
use this term with caution. HP Procurve switches use
"trunk" to define a group of physical Ethernet ports, you trunk
VLAN's from one phyical port to another, Cisco calls
this a channel-group. Cisco uses VLAN trunk as a basic term to define what HP Procurve calls a Tagged port.
VLAN ID
Both
devices use 802.1Q standard VLAN identification. Older HP Procurve
switches which are quite common, such as the HP Procurve
4000m, could only support a maximum of 8 VLANs. This basic feature when
enabled, can add a little more functionality to an otherwise outdated, simple
10/100 switch. To enable VLAN support on your 4000m, you can easily telnet into
the device, login as a manager, and turn on VLAN Support from the menu (it does
require a reboot on these older switches). Today, you can setup up to 256 VLANs
on a single modern HP Procurve switch (or router),
however, a centrally located device, can pass (store) the tags of up to 4096
VLAN ids. VLAN 1 is the default administrative VLAN, this is set as
"Untagged" on all ports out of the box. I generally leave it untagged
on at least each uplink port, this save you from a tag mismatch conundrum (you
may only have one VLAN in "untagged" in HP Procurve
speak (access in Cisco speak) on any one port, which more or less requires
every other VLAN to be "tagged" ("trunked" in Cisco speak)
and passed on to the the next switch or router on an
uplink port.
VLAN
Names
HP Procurve switches allow up to 32 characters for the
description, when you're looking at it in the menu view however, it will be
truncated to 12 characters, so first 12 characters should begin with different
descriptors so that there is some immediate distinction here. Typically, when I
name them, I'll either call them the building or location they are located at,
plus the number ID, e.g. building12. It's good to have both pieces of physical
and virtual information to save yourself some confusion, and early on, so if
you're viewing them in the truncated view, you'll be able to quickly
distinguish the difference.
Final
words of wisdom, keep it simple, and avoid "spaghetti VLAN's". Feel
free to contact us for consultation or advice with your HP and Cisco
integration, we have years of experience building networks with both HP and
Cisco equipment. Remote support is available and we have the ability to
contract onsite.
An untagged
port in a VLAN is a physical member of that VLAN, ie.
when you plug your host into that port, it is physically connected to
that VLAN
(In
Cisco terminology known as "access port").
A tagged
port will normally carry traffic for multiple VLANs from the switch to
other network devices such as an upstream router or an edge switch
(In
Cisco terminology this is called trunking, HP have no
specific term for it).
For
better understanding you must read this explanation: http://en.wikipedia.org/wiki/IEEE_802.1Q
LACP (Link Aggregation Control Protocol)
Link
Aggregation Control Protocol or LACP is one element of an IEEE specification
(802.3ad) that provides guidance on the practice of link aggregation for data
connections.
Importantly,
LACP typically applies to strategies that bundle individual links of Ethernet
connections, and not wireless transfers.
MPLS (Multiprotocol Label Switching)
Is a
mechanism in high-performance telecommunications networks that directs data
from one network node to the next based on short path labels rather than long
network addresses, avoiding complex lookups in a routing table. The labels
identify virtual links (paths) between distant nodes rather than endpoints.
MPLS can encapsulate packets of various network protocols. MPLS supports a
range of access technologies, including T1/E1, ATM, Frame Relay, and DSL.
Round-robin
In general,
round-robin refers to a pattern or ordering whereby items are encountered or
processed sequentially, often beginning again at the start in a circular
manner.
Round-robin
may refer to:
Round-robin bet, a type of
wager offered by UK bookmakers, covering three selections
Round-robin (document), a
document signed by several parties in a circle in order to hide the identity of
the leader
Round-robin DNS, a technique
for dealing with redundant Internet Protocol service hosts
Round-robin letter, a
news-filled letter typically accompanying a Christmas card
Round-robin networks,
communications networks made up of radio nodes organized in a mesh topology
Round-robin scheduling, an
algorithm used in computer science
Round-robin start, a
possible ordering of turns in a turn-based game
Round-robin story, a
collaborative piece of fiction or storytelling
Round robin test, an
interlaboratory test performed independently several times
Round-robin tournament, a
competition where each contestant meets all other contestants in turn.
SFP
port
 Small form-factor
pluggable, or SFP, devices are hot-swappable interfaces used primarily in
network and storage switches. The SFP ports on a switch and SFP modules enable
the switch to connect to fiber and Ethernet cables of different types and
speeds.
Small form-factor
pluggable, or SFP, devices are hot-swappable interfaces used primarily in
network and storage switches. The SFP ports on a switch and SFP modules enable
the switch to connect to fiber and Ethernet cables of different types and
speeds.
----- End of Switching
--------------------------------------------
UEFI (Unified Extensible Firmware Interface), BIOS new generation :
Bios
evolved, DD+ 2,2 To, drv 64 bits, restart faster
after deep sleep,
The
traditional BIOS still has serious limitations. It can only boot from
drives of 2.1 TB or less. 3 TB drives are now common, and a computer
with a BIOS can’t boot from them. That limitation is due to the way the
BIOS’s Master Boot Record system works.
The BIOS
must run in 16-bit processor mode, and only has 1 MB of space to execute
in. It has trouble initializing multiple hardware devices at once, which leads
to a slower boot process when initializing all the hardware interfaces and
devices on a modern PC.
The BIOS
has needed replacement for a long time. Intel started work on the Extensible
Firmware Interface (EFI) specification back in 1998. Apple chose EFI when it
switched to the Intel architecture on its Macs in 2006, but other PC
manufacturers didn’t follow.
In 2007,
Intel, AMD, Microsoft, and PC manufacturers agreed on a new Unified Extensible
Firmware
Interface
(UEFI) specification. This is an
industry-wide standard managed by the Unified Extended Firmware Interface
Forum, and isn’t solely driven by Intel. UEFI support was introduced to
Windows with Windows Vista Service Pack 1 and Windows 7. The vast majority of
computers you can buy today now use UEFI rather than a traditional BIOS.
Open Shortest Path First (OSPF)
Is a routing protocol for Internet
Protocol (IP) networks. It uses a link state routing (LSR) algorithm and falls
into the group of interior gateway protocols (IGPs), operating within a single
autonomous system (AS).
OSPF
gathers link state information from available routers and constructs a topology
map of the network. The topology is presented as a routing table to the
Internet Layer for routing packets by their destination IP address. OSPF
supports Internet Protocol Version 4 (IPv4) and Internet Protocol Version 6
(IPv6) networks and supports the Classless Inter-Domain Routing (CIDR)
addressing model.
OSPF is
widely used in large enterprise networks. IS-IS, another LSR-based protocol, is
more common in large service provider networks.
Originally
designed in the 1980s, OSPF is defined for IPv4 in protocol version 2 by RFC
2328 (1998). The updates for IPv6 are specified as OSPF Version 3 in RFC 5340
(2008). OSPF supports the Classless Inter-Domain Routing (CIDR) addressing
model.
-LAN Authentication
WPA Personal:
Wi-Fi
Protected Access (WPA and WPA2) is a class of systems to secure
wireless (Wi-Fi) computer networks.In the
"Personal" mode, the most likely choice for homes and small offices,
a passphrase is required.it can also be used in a with/less
secure "pre-shared key" (PSK) mode.
WPA Enterprise:
A router
(or Wi-Fi router) feature that is designed to authenticate individual users to
an external server via username and password. WPA Enterprise also gives each PC
a unique encryption key, which the user never sees, so they can't share it. To
use WPA/WPA2 Enterprise you need a RADIUS server.
WPA2:
Short
for Wi-Fi Protected Access 2, the follow on security method to
WPA for wireless networks that provides stronger data protection and network
access control. It provides enterprise and consumer Wi-Fi users with a high
level of assurance that only authorized users can access their wireless
networks. Based on the IEEE 802.11i standard, WPA2 provides government grade
security by implementing the National Institute of Standards and Technology
(NIST) FIPS 140-2 compliant AES encryption algorithm and 802.1x-based authentication. [Adapted from Wi-Fi.org]
There
are two versions of WPA2: WPA2-Personal, and WPA2-Enterprise. WPA2-Personal protects
unauthorized network access by utilizing a set-up password. WPA2-Enterprise
verifies network users through a server. WPA2 is backward compatible with WPA.
WEP:
Wired
Equivalent Privacy or Wireless Encryption pejim (WEP) is a scheme to secure IEEE 802.11
wireless networks. It is part of the IEEE 802.11
wireless networking standard. Wireless networks broadcast messages using radio, so are more
susceptible to eavesdropping than wired networks. WEP was
intended to provide confidentiality comparable to that of a
traditional wired network. Several serious weaknesses were
identified by cryptanalysts; a WEP connection can be cracked
with readily available software within minutes. WEP was superseded by Wi-Fi Protected Access (WPA) in 2003, followed by the full
IEEE 802.11i
standard (also known as WPA2) in 2004. Despite its weaknesses, WEP provides a level of security
that may deter casual snooping.
Radius:
Short
for Remote Authentication Dial-In User Service, an authentication and
accounting system used by many Internet Service Providers (ISPs). When you dial
in to the ISP you must enter your username and password. This information is
passed to a RADIUS server, which checks that the information is correct, and
then authorizes access
EAP (Extensible
Authentication Protocol):
Is an
authentication framework frequently used in network and internet connections.
It is
defined in RFC 3748, which made RFC 2284 obsolete, and is updated by RFC 5247.
EAP is
an authentication framework for providing the transport and usage of material
and parameters generated by EAP methods.
There
are many methods defined by RFCs, and a number of vendor-specific methods and
new proposals exist. EAP is not a wire protocol; instead, it only defines the
information from the interface and the formats. Each protocol that uses EAP
defines a way to encapsulate by the user EAP messages within that protocol's
messages.
EAP is
in wide use. For example, in IEEE 802.11 (WiFi) the
WPA and WPA2 standards have adopted IEEE 802.1X (with various EAP types) as the
canonical authentication mechanism.
IEEE 802.1X
Is an
IEEE Standard for port-based Network Access Control (PNAC). It is part of the
IEEE 802.1 group of networking protocols. It provides an authentication
mechanism to devices wishing to attach to a LAN or WLAN.
IEEE
802.1X defines the encapsulation of the Extensible Authentication Protocol
(EAP) over IEEE 802.11, which is known as "EAP over LAN" or EAPOL.
EAPOL
was originally designed for IEEE 802.3 Ethernet in 802.1X-2001 but was
clarified to suit other IEEE 802 LAN technologies such as IEEE 802.11 wireless
and Fiber Distributed Data Interface (ANSI X3T9.5/X3T12 and ISO 9314) in
802.1X-2004. The EAPOL was also modified for use with IEEE 802.1AE
("MACsec") and IEEE 802.1AR (Secure Device Identity, DevID) in
802.1X-2010 to support service identification and optional point to point
encryption over the internal LAN segment.
-Data Ciphering (Encryption)
TKIP:
Temporal
Key Integrity Protocol is a security protocol used in Wi-Fi Protected
Access (WPA).
AES:
Cryptography,
the Advanced Encryption Standard (AES), also known as Rijndael,
is a block cipher adopted as an encryption standard by the U.S. government.
CCMP:
Counter
Mode with Cipher Block Chaining Message Authentication Code Protocol,
is an IEEE 802.11i encryption protocol, created to replace, together with TKIP,
an earlier, insecure WEP protocol.
-VPN Passthrough:
PPTP:
Short
for Point-to-Point Tunneling Protocol, a new technology for
creating Virtual Private Networks (VPNs), developed jointly by Microsoft
Corporation, U.S. Robotics, and several remote access vendor companies, known
collectively as the PPTP Forum
L2TP:
Short
for Layer Two (2) Tunneling Protocol, an extension to the PPP
protocol that enables ISPs to operate Virtual Private Networks (VPNs).L2TP
merges the best features of two other tunneling protocols: PPTP from Microsoft
and L2F from Cisco Systems. Like PPTP, L2TP requires that the ISP's routers
support the protocol.
IPSEC:
Short
for IP Security, a set of protocols developed by the IETF to
support secure exchange of packets at the IP layer. IPsec has been deployed
widely to implement Virtual Private Networks (VPNs).IPsec supports two
encryption modes: Transport and Tunnel. Transport mode encrypts only the data
portion (payload) of each packet, but leaves the header untouched. The more
secure Tunnel mode encrypts both the header and the payload. On the receiving
side, an IPSec-compliant device decrypts each packet.
For
IPsec to work, the sending and receiving devices must share a public key. This
is accomplished through a protocol known as Internet Security Association and
Key Management Protocol/Oakley (ISAKMP/Oakley), which allows the receiver to
obtain a public key and authenticate the sender using digital certificates
Cryptographic Algorithms and Protocols
IPESEC,
TLS(SSL), SSH, S/MIME, OpenPGP/GnuPG/PGP, and Kerberos
Symmetric Key Encryption Algorithms
AES,
3DES
RSA
(only in USA)
MD5,
SHA0, SHA-256 / SHA-384 / SHA-512, SHA-3
Integrity Checking
The usual approach is “HMAC”,
which computes the integrity check as
H(k xor opad, H(k xor
ipad, data))
where H is
the hash function and k is the key. This is defined in detail in IETF RFC 2104
Randomized Message Authentication Mode (RMAC)
HMAC-SHA1
OPAQUE
protocol,
a secure
asymmetric Password
Authenticated Key
Exchange (aPAKE)
that supports mutual authentication in a client-server setting without reliance
on PKI and with security against pre-computation attacks upon server
compromise.
The
OPAQUE protocol is an asymmetric password-authenticated key exchange, PAKE.
A PAKE
is a way to exchange cryptographic keys with the knowledge of a password. The
asymmetric part of this aPAKE means that only one
party knows the actual password; the password does not have to be revealed to
both parties taking part in the exchange.
-Types Authentication:
EAP-SIM :
Extensible
Authentication Protocol Method for GSM Subscriber Identity, is an Extensible
Authentication Protocol (EAP) mechanism for authentication and session key
distribution using the Global System for Mobile Communications (GSM) Subscriber
Identity Module (SIM). EAP-SIM is described in RFC 4186.
TLS (SSL)
Transport
Layer Security (TLS) and its predecessor, Secure Sockets Layer (SSL), are cryptographic
protocols that provide communication security
over the Internet.[1]
They use asymmetric cryptography for authentication
of key exchange, symmetric encryption for confidentiality
and message authentication codes for message
integrity. Several versions of the protocols are in widespread use in
applications such as web browsing, electronic mail,
Internet
faxing, instant messaging and voice-over-IP (VoIP).
TTLS:
Tunnelled
Transport Layer Security, It was co-developed by Funk Software and Certicom. It is widely supported across platforms, and
offers very good security. The client does not need be authenticated via a
CA-signed PKI certificate to the server, but only the server to the client.
This greatly simplifies the setup procedure as a certificate does not need to
be installed on every client.
LEAP:
Lightweight
Extensible Authentication Protocol is a
proprietary wireless LAN authentication method developed by Cisco Systems.
PEAP:
Extensible
Authentication Protocol, Protected EAP, or simply (pronounced
"peep"), is a method to securely transmit authentication information,
including passwords, over wired or wireless networks.
EAP:
Extensible
Authentication Protocol is a universal authentication framework
frequently used in wireless networks and Point-to-Point connections. It is
defined by RFC 3748.
-Protocol Authentication:
PEAPv1/EAP-GTC
Was
created by Cisco as an alternative to PEAPv0/EAP-MSCHAPv2. It allows the use of
an inner authentication protocol other than Microsoft's MSCHAPv2. EAP-GTC
(Generic Token Card) is defined in RFC 3748.
SHA-1
In
cryptography, SHA-1 is a cryptographic hash function designed by the United
States National Security Agency and is a U.S. Federal Information Processing
Standard published by the United States NIST.
SHA-1
produces a 160-bit (20-byte) hash value. A SHA-1 hash value is typically
rendered as a hexadecimal number, 40 digits long.
SHA
stands for "secure hash algorithm". The four SHA algorithms are structured
differently and are named SHA-0, SHA-1, SHA-2, and SHA-3. SHA-0 is the original
version of the 160-bit hash function published in 1993 under the name
"SHA": it was not adopted by many applications. Published in 1995,
SHA-1 is very similar to SHA-0, but alters the original SHA hash specification
to correct alleged weaknesses. SHA-2, published in 2001, is significantly
different from the SHA-1 hash function.
SHA-1 is
the most widely used of the existing SHA hash functions, and is employed in
several widely used applications and protocols.
In 2005,
cryptanalysts found attacks on SHA-1 suggesting that the algorithm might not be
secure enough for ongoing use. NIST required many applications in federal
agencies to move to SHA-2 after 2010 because of the weakness. Although no
successful attacks have yet been reported on SHA-2, it is algorithmically
similar to SHA-1. In 2012, following a long-running competition, NIST selected
an additional algorithm, Keccak, for standardization under SHA-3. In November
2013 Microsoft announced their deprecation policy on SHA-1 according to which
Windows will stop accepting SHA-1 certificates in SSL by 2017. In September
2014 Google announced their deprecation policy on SHA-1 according to which
Chrome will stop accepting SHA-1 certificates in SSL in a phased way by 2017.
Mozilla is also planning to stop accepting SHA-1-based SSL certificates by
2017.
MD5
The MD5
message-digest algorithm is a widely used cryptographic hash function producing
a 128-bit (16-byte) hash value, typically expressed in text format as a 32
digit hexadecimal number. MD5 has been utilized in a wide variety of
cryptographic applications, and is also commonly used to verify data integrity.
MD5 was
designed by Ron Rivest in 1991 to replace an earlier hash function, MD4. The
source code in RFC 1321 contains a "by attribution" RSA license.
In 1996
a flaw was found in the design of MD5. While it was not deemed a fatal weakness
at the time, cryptographers began recommending the use of other algorithms,
such as SHA-1—which has since been found to be vulnerable as well. In
2004 it was shown that MD5 is not collision resistant. As such, MD5 is not
suitable for applications like SSL certificates or digital signatures that rely
on this property for digital security. Also in 2004 more serious flaws were
discovered in MD5, making further use of the algorithm for security purposes
questionable; specifically, a group of researchers described how to create a
pair of files that share the same MD5 checksum. Further advances were made in
breaking MD5 in 2005, 2006, and 2007. In December 2008, a group of researchers
used this technique to fake SSL certificate validity, and CMU Software
Engineering Institute now says that MD5 "should be considered
cryptographically broken and unsuitable for further use", and most U.S.
government applications now require the SHA-2 family of hash functions. In
2012, the Flame malware exploited the weaknesses in MD5 to fake a Microsoft
digital signature.
Quantum cryptography
Quantum
cryptography sounds fairly complex – probably because it is. That’s
why we put together this “encryption guide for dummies” as a way of
explaining what quantum cryptography is and taking some of the complexity out
of it.
Although
the subject has been around for a couple of decades, quantum cryptography (not
to be confused with post-quantum cryptography) is quickly becoming more
critically relevant to our everyday lives because of how it can safeguard vital
data in a way that current encryption methods can’t.
Consider,
for example, the trust you place in banks and commercial enterprises to keep
your credit card and other information safe while conducting business
transactions online. What if those companies – using current encryption
methods – could no longer guarantee the security of your private
information? Granted, cybercriminals are always trying to gain access to secure
data, but when quantum computers come online, that information will be even
more vulnerable to being hacked. In fact, hackers don’t even need to wait
for quantum computers to start the process because they’re collecting
encrypted data now to decrypt later when the quantum computers are ready. With
quantum encryption, that’s not the case because your information will be unhackable. Let’s explain.
What is
Quantum Cryptography?
Cryptography
is the process of encrypting data, or converting plain text into scrambled text
so that only someone who has the right “key” can read it. Quantum
cryptography, by extension, simply uses the principles of quantum mechanics to
encrypt data and transmit it in a way that cannot be hacked.
While
the definition sounds simple, the complexity lies in the principles of quantum
mechanics behind quantum cryptography, such as:
The
particles that make up the universe are inherently uncertain and can
simultaneously exist in more than one place or more than one state of being.
Photons
are generated randomly in one of two quantum states.
You
can’t measure a quantum property without changing or disturbing it.
You can
clone some quantum properties of a particle, but not the whole particle.
All
these principles play a role in how quantum cryptography works.
What’s
the difference between post-quantum cryptography and quantum cryptography?
Post-quantum
cryptography refers to cryptographic algorithms (usually public-key algorithms)
that are thought to be secure against an attack by a quantum computer. These
complex mathematical equations take traditional computers months or even years
to break. However, quantum computers running Shor’s algorithm will be
able to break math-based systems in moments.
Quantum
cryptography, on the other hand, uses the principles of quantum mechanics to
send secure messages, and unlike mathematical encryption, is truly un-hackable.
‘Unlike
mathematical encryption, quantum cryptography uses the principles of quantum
mechanics to encrypt data and making it virtually unhackable.’
How
Quantum Cryptography Works
Quantum
cryptography, or quantum key distribution (QKD), uses a series of photons
(light particles) to transmit data from one location to another over a fiber
optic cable. By comparing measurements of the properties of a fraction of these
photons, the two endpoints can determine what the key is and if it is safe to
use.
Breaking
the process down further helps to explain it better.
The
sender transmits photons through a filter (or polarizer) which randomly gives
them one of four possible polarizations and bit designations: Vertical (One
bit), Horizontal (Zero bit), 45 degree right (One bit), or 45 degree left (Zero
bit).
The
photons travel to a receiver, which uses two beam splitters
(horizontal/vertical and diagonal) to “read” the polarization of
each photon. The receiver does not know which beam splitter to use for each
photon and has to guess which one to use.
Once the
stream of photons has been sent, the receiver tells the sender which beam
splitter was used for each of the photons in the sequence they were sent, and
the sender compares that information with the sequence of polarizers used to
send the key. The photons that were read using the wrong beam splitter are
discarded, and the resulting sequence of bits becomes the key.
If the
photon is read or copied in any way by an eavesdropper, the photon’s
state will change. The change will
be detected by the endpoints. In other words, this means you cannot read the
photon and forward it on or make a copy of it without being detected.
An
example of how quantum encryption works:
Imagine
you have two people, Alice and Bob, who want to send a secret to each other
that no one else can intercept. With QKD, Alice sends Bob a series of polarized
photons over a fiber optic cable. This cable doesn’t need to be secured
because the photons have a randomized quantum state.
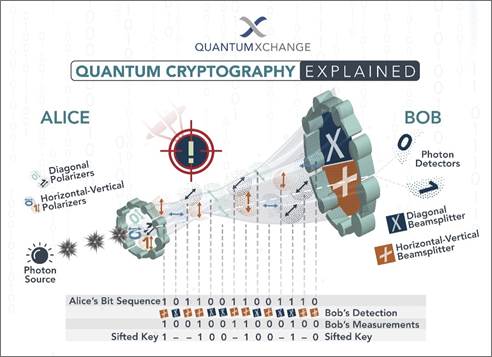
How
quantum cryptography works explained
If an
eavesdropper, named Eve, tries to listen in on the conversation, she has to
read each photon to read the secret. Then she must pass that photon on to Bob.
By reading the photon, Eve alters the photon’s quantum state, which
introduces errors into the quantum key. This alerts Alice and Bob that someone
is listening and the key has been compromised, so they discard the key. Alice
has to send Bob a new key that isn’t compromised, and then Bob can use
that key to read the secret.
The
Solution We Need Now for Tomorrow
The need
for unbreakable encryption is staring us in the face. With the development of
quantum computers looming on the horizon, the integrity of encrypted data is at
risk now. Fortunately, quantum cryptography, through QKD, offers the solution
we need to safeguard our information well into the future – all based on
the complex principles of quantum mechanics.
‘As
the need for unbreakable encryption looms in networks around the world, quantum
cryptography is the solution that will safeguard and future-proof sensitive
information.’
Network Monitoring
PRTG
PRTG
Network Monitor (Paessler Router Traffic Grapher until version 7) is an agentless network monitoring
software from Paessler AG. It can monitor and
classify system conditions like bandwidth usage or uptime and collect
statistics from miscellaneous hosts as switches, routers, servers and other
devices and applications.
The
first version of PRTG was released on 29 May 2003 by the German company Paessler GmbH (now: Paessler AG),
which was founded by Dirk Paessler in 2001
Collect protocols
For
scanning the predefined areas of an enterprise network and creates a device
list from these data, the information on the detected devices can be retrieved
using the various communication protocols.
Ping,
Ping
measures the round-trip time for messages sent from the originating host to a
destination computer
SNMP,
An
Internet Standard protocol for collecting and organizing information about
managed devices on IP networks and for modifying that information to change
device behavior.
WMI,
Consists
of a set of extensions to the Windows Driver Model that provides an operating
system interface through which instrumented components provide information and
notification.
WMI is
Microsoft's implementation of the Web-Based Enterprise Management (WBEM)
and Common Information Model (CIM) standards from the Distributed
Management Task Force (DMTF).
WMI
allows scripting languages (such as VBScript or Windows PowerShell) to manage
Microsoft Windows personal computers and servers, both locally and remotely.
WMI
comes preinstalled in Windows 2000 and in newer Microsoft OSes. It is available
as a download for Windows NT and Windows 95 to Windows 98.
Microsoft
also provides a command-line interface to WMI called Windows Management
Instrumentation Command-line (WMIC).
NetFlow,
Is a
feature that was introduced on Cisco routers around 1996 that provides the
ability to collect IP network traffic as it enters or exits an interface.
jFlow,
sFlow,
Short
for "sampled flow", is an industry standard for packet export at
Layer 2 of the OSI model. It provides a means for exporting truncated packets,
together with interface counters for the purpose of network monitoring.
Maintenance
of the protocol is performed by the sFlow.org consortium
DICOM,
Digital
Imaging and Communications in Medicine (DICOM) is the standard for the
communication and management of medical imaging information and related data.
It is
most commonly used for storing and transmitting medical images enabling the
integration of medical imaging devices such as scanners, servers, workstations,
printers, network hardware, and picture archiving and communication systems (PACS)
from multiple manufacturers.
It has been
widely adopted by hospitals and is making inroads into smaller applications
such as dentists' and doctors' offices.
RESTful
API,
Representational
state transfer (REST) is a software architectural style that was created
to guide the design and development of the architecture for the World Wide Web.
REST defines a set of constraints for how the architecture of an Internet-scale
distributed hypermedia system, such as the Web, should behave. The REST
architectural style emphasises the scalability of
interactions between components, uniform interfaces, independent deployment of
components, and the creation of a layered architecture to facilitate caching
components to reduce user-perceived latency, enforce security, and encapsulate
legacy systems.
REST has
been employed throughout the software industry and is a widely accepted set of
guidelines for creating stateless, reliable web APIs. A web API that obeys the
REST constraints is informally described as RESTful. RESTful web APIs are
typically loosely based on HTTP methods to access resources via URL-encoded
parameters and the use of JSON or XML to transmit data.
Mail Protocol:
SMTP:
Simple Mail Transfer Protocol is an Internet standard for electronic mail (e-mail) transmission across Internet Protocol (IP) networks. SMTP was
first defined by RFC 821
(1982, eventually declared STD 10),[1]
and last updated by RFC 5321
ESMTP:
Extended SMTP (ESMTP), sometimes referred to as Enhanced
SMTP, is a definition of protocol extensions to the Simple Mail
Transfer Protocol standard. The extension format was defined in IETF publication RFC 1869 (1995) which established a
general structure for all existing and future extensions.
QMTP:
The Quick Mail Transfer Protocol is an e-mail transmission protocol
that is designed to have better performance than Simple Mail
Transfer Protocol (SMTP), the de facto standard. It was designed and
implemented by Daniel J. Bernstein.
NNFMP:
Is an internal protocol not recognized
by IANA or the RFCs. Yahoo uses this
protocol to internally route email traffic across their network. The initialism stands for "Newman No-Frills Mail Protocol".
It is a simple, high-performance protocol comparable to QMTP. However, Yahoo will not officially recognize its use
POP3 :
Post Office Protocol récupére
les courriers
électroniques situés sur un serveur de messagerie électronique. Actuellement, c'est POP3, qui est utilisé de
façon standard. Il est défini dans la RFC 1939.
Commandes principales :
DELE numéro_du_message :
efface le message spécifié
LIST : donne une liste des
messages ainsi que la taille de chaque message : un numéro suivi de
la taille en octets.
RETR numéro_du_message :
récupère le message indiqué
STAT : indique le nombre de messages et la taille
occupée par l'ensemble des messages
TOP numéro_du_message
nombre_de_lignes : affiche les premières
lignes du message.
Autres commandes POP3
APOP : permet une authentification
sécurisée (le mot de passe ne transite pas en clair)
NOOP : ne rien faire, utile pour ne pas perdre la
connexion et éviter un « délai d'attente
dépassé »
QUIT : quitter la session
en cours
RSET : réinitialise complètement la
session
UIDL : affiche (pour un seul ou pour tous les
messages) un identifiant unique qui ne varie pas entre chaque session
CAPA : affiche les informations du serveur
IMAP :
The Internet
Message Access Protocol (commonly known as IMAP) is an Application
Layer Internet protocol that allows an e-mail client
to access e-mail
on a remote mail server. The current version, IMAP version
4 revision 1 (IMAP4rev1), is defined by RFC
3501. An IMAP server typically listens on well-known port 143. IMAP
over SSL (IMAPS) is assigned well-known port
number 993.
DNS record
SPF1:
The design intent of the SPF resource record (RR) is to allow a receiving MTA
(Message Transfer Agent) to interrogate the Name Server (DNS) of the domain,
which appears in the email (the sender) and determine if the originating IP of
the mail (the source) is authorized to send mail for the sender's domain. The
mail sender is required to publish an SPF TXT RR in the DNS zone file for their
domain but this is transparent to the sending MTA. That is, the sending MTA
does not use the sending domain's SPF RR(s) but the receiving domain's MTA will
interrogate and use the sending domain's SPF RR(s).
The SPF
information must be defined using a standard TXT resource record (RR).
1-
For
decreasing the spam, RFC 4408 introduced the standard SPF (Sender
Policy Framework)
An SPF (Sender Policy Framework) record is a type of TXT record in your DNS
zone file. SPF records help identify which mail servers are permitted to send
email on behalf of your domain. Adding an SPF record can help detect and
prevent spammers from sending email messages with forged From addresses on your
domain.
DKIM
DomainKeys
Identified Mail (DKIM) is an email authentication method designed to detect
forged sender addresses in email (email spoofing), a technique often used in
phishing and email spam.
DKIM
allows the receiver to check that an email claimed to have come from a specific
domain was indeed authorized by the owner of that domain. It achieves this by
affixing a digital signature, linked to a domain name, to each outgoing email
message. The recipient system can verify this by looking up the sender's public
key published in the DNS. A valid signature also guarantees that some parts of
the email (possibly including attachments) have not been modified since the
signature was affixed. Usually, DKIM signatures are not visible to end-users,
and are affixed or verified by the infrastructure rather than the message's
authors and recipients.
DKIM is
an Internet Standard. It is defined in RFC 6376, dated September 2011; with
updates in RFC 8301 and RFC 8463.
RBL
Short
for Realtime Blackhole
List, a list of IP addresses whose owners
refuse to stop the proliferation of spam. The RBL usually lists server IP
addresses from ISPswhose customers are responsible
for the spam and from ISPs whose servers are hijacked for spam relay.
As
subscribers to the RBL, ISPs and companies will know from which IP addresses to
block traffic. Most traffic blocking occurs during the SMTP connection phase.
The receiving end will check the RBL for the connecting IP address. If the IP
address matches one on the list, then the connection gets dropped before
accepting any traffic from the spammer. Some ISPs, though, will choose to
blackhole (or ignore) IP packets at their routers. The goal here is to block
all IP traffic.
It is
important to note that all e-mail and packet blocking is done by the recipient,
not the RBL administrator, which is only responsible for bouncing spam that is
directed at its servers.
Cyber Security, Types of Attacks
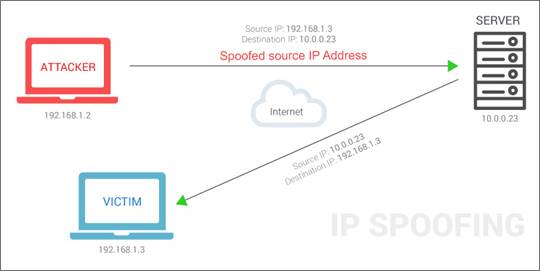
IP SPOOFING
The data transmitted over the internet is first
broken into multiple packets, and those packets are transmitted independently
and reassembled at the end. Each packet has an IP (Internet Protocol) header
that contains information about the packet, including the source IP address and
the destination IP address.
In IP spoofing, a hacker uses tools to modify
the source address in the packet header to make the receiving computer system
think the packet is from a trusted source, such as another computer on a
legitimate network, and accept it. Because this occurs at the network level,
there are no external signs of tampering.
This type of attack is common in
Denial-of-Service (DoS) attacks, which can overwhelm computer networks with
traffic. In a DoS attack, hackers use spoofed IP addresses to overwhelm
computer servers with packets of data, shutting them down.
The source IP address:
Is normally the address that the packet was
sent from, but the sender's address in the header can be altered, so that to
the recipient it appears that the packet came from another source.
The protocol requires the receiving computer to
send back a response to the source IP address, so that spoofing is mainly used
when the sender can anticipate the network response or does not care about the
response.
The source IP address provides only limited
information about the sender.
It may provide general information on the
region, city and town when on the packet was sent. It does not provide
information on the identity of the sender or the computer being used.
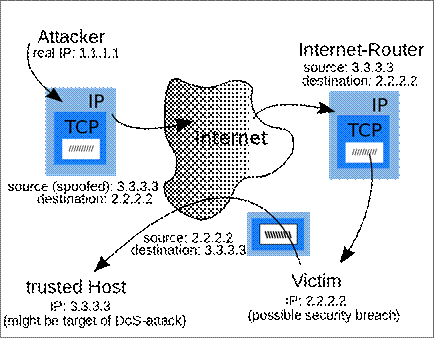
This is
an example of IP SPOOFING
DDos
(Denial-of-service attack)
In
computing, a denial-of-service (DoS) attack is an attempt to make a machine or
network resource unavailable to its intended users, such as to temporarily or
indefinitely interrupt or suspend services of a host connected to the Internet.
A distributed denial-of-service (DDoS) is where the attack source is more than
one–and often thousands–of unique IP addresses.
Criminal
perpetrators of DoS attacks often target sites or services hosted on
high-profile web servers such as banks, credit card payment gateways; but
motives of revenge, blackmail or activism can be behind other attacks.
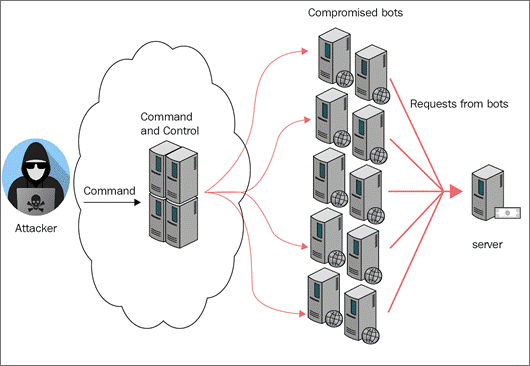
DDoS
Stacheldraht attack diagram
Stacheldraht (German
for barbed wire) is a piece of software written by Random for Linux and Solaris
systems which acts as a distributed denial of service (DDoS) agent. This tool
detects and automatically enables source address forgery.
Stacheldraht uses a
number of different DoS attacks, including UDP flood, ICMP flood, TCP SYN
flood and Smurf attack.
It
combines features of Trinoo with TFN,
and adds encryption.
Hijacking
In
computer science, session hijacking, sometimes also known as cookie hijacking
is the exploitation of a valid computer session—sometimes also called a
session key—to gain unauthorized access to information or services in a
computer system. In particular, it is used to refer to the theft of a magic
cookie used to authenticate a user to a remote server. It has particular
relevance to web developers, as the HTTP cookies used to maintain a session on
many web sites can be easily stolen by an attacker using an intermediary
computer or with access to the saved cookies on the victim's computer (see HTTP
cookie theft).
A
popular method is using source-routed IP packets. This allows an attacker at
point B on the network to participate in a conversation between A and C by
encouraging the IP packets to pass through B's machine.
If
source-routing is turned off, the attacker can use "blind" hijacking,
whereby it guesses the responses of the two machines. Thus, the attacker can
send a command, but can never see the response. However, a common command would
be to set a password allowing access from somewhere else on the net.
An
attacker can also be "inline" between A and C using a sniffing
program to watch the conversation. This is known as a "man-in-the-middle
attack".
Spoofing
In the
context of network security, a spoofing attack is a situation in which one
person or program successfully masquerades as another by falsifying data and
thereby gaining an illegitimate advantage.
Spoofing and TCP/IP
Many of
the protocols in the TCP/IP suite do not provide mechanisms for authenticating
the source or destination of a message. They are thus vulnerable to spoofing
attacks when extra precautions are not taken by applications to verify the
identity of the sending or receiving host. IP spoofing and ARP spoofing in
particular may be used to leverage man-in-the-middle attacks against hosts on a
computer network. Spoofing attacks which take advantage of TCP/IP suite
protocols may be mitigated with the use of firewalls capable of deep packet
inspection or by taking measures to verify the identity of the sender or
recipient of a message.
Fishing
Phishing
is the attempt to acquire sensitive information such as usernames, passwords,
and credit card details (and sometimes, indirectly, money), often for malicious
reasons, by masquerading as a trustworthy entity in an electronic
communication. The word is a neologism created as a homophone of fishing due to
the similarity of using fake bait in an attempt to catch a victim.
Communications purporting to be from popular social web sites, auction sites,
banks, online payment processors or IT administrators are commonly used to lure
unsuspecting victims. Phishing emails may contain links to websites that are
infected with malware. Phishing is typically carried out by email spoofing or
instant messaging, and it often directs users to enter details at a fake website
whose look and feel are almost identical to the legitimate one. Phishing is an
example of social engineering techniques used to deceive users, and exploits
the poor usability of current web security technologies. Attempts to deal with
the growing number of reported phishing incidents include legislation, user
training, public awareness, and technical security measures. Many websites have
now created secondary tools for applications, like maps for games, but they
should be clearly marked as to who wrote them, and users should not use the
same passwords anywhere on the internet.
Identity theft
Identity theft is a crime in which an imposter obtains key pieces of personal information, such as Social Security or driver's license numbers, in order to impersonate someone else. The information can be used to obtain credit, merchandise, and services in the name of the victim, or to provide the thief with false credentials. In addition to running up debt, an imposter might provide false identification to police, creating a criminal record or leaving outstanding arrest warrants for the person whose identity has been stolen.
Identity theft is categorized in two ways: true name and account takeover. True name identity theft means that the thief uses personal information to open new accounts. The thief might open a new credit card account, establish cellular phone service, or open a new checking account in order to obtain blank checks. Account takeover identity theft means the imposter uses personal information to gain access to the person's existing accounts. Typically, the thief will change the mailing address on an account and run up a huge bill before the person whose identity has been stolen realizes there is a problem. The Internet has made it easier for an identity thief to use the information they've stolen because transactions can be made without any personal interaction.
Bootkit / RootKit
It is a
collection of computer software, typically malicious, designed to enable access
to a computer or areas of its software that would not otherwise be allowed (for
example, to an unauthorized user) and often masks its existence or the
existence of other software. The word is a concatenation of "root"
(the traditional name of the privileged account on Unix-like operating systems)
and the word "kit" (which refers to the software components that
implement the tool).
Network Behavior anomaly detection (NBAD)
It
provides one approach to network security threat detection. It is a
complementary technology to systems that detect security threats, based on
packet signatures.
NBAD is
the continuous monitoring of a network for unusual events or trends. NBAD is an
integral part of network behavior analysis (NBA), which offers security in
addition to that provided by traditional anti-threat applications such as
firewalls, intrusion detection systems, antivirus software and
spyware-detection software.
Eavesdrop
An
eavesdropping attack, which are also known as a sniffing or snooping attack, is
an incursion where someone tries to steal information that computers,
smartphones, or other devices transmit over a network. An eavesdropping attack
takes advantage of unsecured network communications in order to access the data
being sent and received. Eavesdropping attacks are difficult to detect because
they do not cause network transmissions to appear to be operating abnormally.
Tamper
Tampering
is one of the biggest security threats faced by web applications. It is used to
change or edit files found in web applications which are usually used by
multi-million business corporations across the world. Tampering started in the
late 1980's as a way to sabotage data or plant a malicious or destructive
program to delete data. Since then it has progressed and enhanced through the
years. In the year 2000, hackers were able to perform data fabrication and
falsification to deceive the uses of the web application.
Forgery
Cross-Site
Request Forgery (CSRF) attacks typically target web applications. CSRF attacks
can include unauthorized changes of user information or extraction of user
sensitive data from a web application.
CSRF
exploits utilize social engineering to convince a user to open a link that,
when processed by the affected web application, could result in arbitrary code
execution. CSRF exploit code can be stored in a web location (for example, a
stored CSRF) in a one-pixel iframe/image or can be a
component of a CSRF exploit. When processed, the CSRF link could allow the
attacker to submit arbitrary requests via the affected web application with the
privileges of the user. The origins of CSRF attacks are difficult to identify
utilizing traceback methods. Social
engineering methods can conceal the attacker's identity because the server is
treating the request as a legitimate request from the user.
Global Threat Intelligence (GTI)
McAfee
Labs publishes timely, relevant threat activity via McAfee Global Threat
Intelligence (GTI). This always-on, cloud-based threat intelligence service
enables accurate protection against known and fast-emerging threats by
providing threat determination and contextual reputation metrics. McAfee GTI
integrates directly with our security products, instantly protecting against
emerging threats to reduce operational efforts and time between detection and
containment.
This is the partial short list of attacks:
Passive
Network
Wiretapping
Port
scanner
Idle
scan
Active
Denial-of-service
attack
Hijacking
Spoofing
Network
Man
in the middle (MitM)
ARP
poisoning
Ping
flood
Ping
of death
Smurf
attack
Host
Buffer
overflow
Heap
overflow
Stack
overflow
Format
string attack
There are many notes gathered in this file: CyberSecurity-Notes.
End Point Protection
EDR :
Endpoint Detection and Response
EPP :
protection EndPoints
EPM :
Endpoint Privilege Manager
RMM :
Remote Monitoring and Management
PSA : Professional
Services Automation
Cloud Computing
SaaS : Software-as-a-service
IaaS : Infrastructure-as-a-service
PaaS :
Platform-as-a-service
CCaaS : Contact Center as a
Service
Components of a SASE Model
SASE can
be broken down into six essential elements in terms of its
capabilities
and technologies:
1- Software-Defined Wide Area Network (SD-WAN)
SD-WAN
is an overlay architecture that reduces complexity and
optimizes
the user experience by selecting the best route for traffic to
the
internet, cloud apps, and the data center. It also helps you rapidly
deploy
new apps and services as well as manage policies across a
large
number of locations.
2- Secure Web Gateway (SWG)
SWGs
prevent unsecured internet traffic from entering your internal
network.
It shields your employees and users from accessing and
being
infected by malicious web traffic, vulnerable websites, internetborne
viruses, malware, and other cyberthreats.
3- Cloud Access Security Broker (CASB)
CASBs
prevent data leaks, malware infection, regulatory
noncompliance,
and lack of visibility by ensuring safe use of cloud
apps and
services. They secure cloud apps hosted in public clouds
(IaaS),
private clouds, or delivered as software-as-a-service (SaaS).
4- Firewall as a Service (FWaaS)
FWaaS helps
you replace physical firewall appliances with cloud
firewalls
that deliver advanced Layer 7/next-generation firewall
(NGFW)
capabilities, including access controls, such as URL filtering,
advanced
threat prevention, intrusion prevention systems (IPS), and
DNS
security.
5- Zero Trust Network Access (ZTNA)
ZTNA
solutions give remote users secure access to internal apps.
With a
zero trust model, trust is never assumed, and least privileged
access
granted based on granular policies. It gives remote users
secure
connectivity without placing them on your network or
exposing
your apps to the internet.
6- Centralized Management
Managing
all of the above from a single console lets you eliminate
many of
the challenges of change control, patch management,
coordinating
outage windows, and policy management while
delivering
consistent policies across your organization, wherever users
connect
from.
Telecommunication
Protocol
H.323
protocol
(MGCP) Media
Gateway Control Protocol
(SIP) Session
Initiation Protocol
(Megaco)) H.248
(also known as Media Gateway Control )
(RTP) Real-time
Transport Protocol
(RTCP) Real-time
Transport Control Protocol
(SRTP) Secure
Real-time Transport Protocol
(SDP) Session
Description Protocol
(IAX) Inter-Asterisk
eXchange
XMPP Jingle
XMPP VoIP extensions
Skype protocol
Teamspeak
EDGE
Enhanced Data
rates for GSM Evolution (EDGE) (also known as Enhanced
GPRS (EGPRS), or IMT Single Carrier (IMT-SC),
or Enhanced Data rates for Global Evolution) is a digital mobile phone
technology that allows improved data transmission rates as a
backward-compatible extension of GSM. EDGE is considered a pre-3G radio
technology and is part of ITU's 3G definition. EDGE was deployed on GSM
networks beginning in 2003 – initially by Cingular (now AT&T) in the
United States.
EDGE is
standardized also by 3GPP as part of the GSM family. A variant, so called
Compact-EDGE, was developed for use in a portion of Digital AMPS network
spectrum.
Through
the introduction of sophisticated methods of coding and transmitting data, EDGE
delivers higher bit-rates per radio channel, resulting in a threefold increase
in capacity and performance compared with an ordinary GSM/GPRS connection.
EDGE can
be used for any packet switched application, such as an Internet
connection.
Evolved
EDGE continues in Release 7 of the 3GPP standard providing reduced
latency and more than doubled performance e.g. to complement High-Speed Packet
Access (HSPA). Peak bit-rates of up to 1 Mbit/s and typical bit-rates of
400 kbit/s can be expected.
3G
3G,
short form of third generation, is the third generation of mobile
telecommunications technology. This is based on a set of standards used for
mobile devices and mobile telecommunications use services and networks that
comply with the International Mobile Telecommunications-2000 (IMT-2000)
specifications by the International Telecommunication Union. 3G finds
application in wireless voice telephony, mobile Internet access, fixed wireless
Internet access, video calls and mobile TV.
3G
telecommunication networks support services that provide an information
transfer rate of at least 200 kbit/s. Later 3G releases, often denoted
3.5G and 3.75G, also provide mobile broadband access of several Mbit/s to
smartphones and mobile modems in laptop computers. This ensures it can be
applied to wireless voice telephony, mobile Internet access, fixed wireless
Internet access, video calls and mobile TV technologies.
A new
generation of cellular standards has appeared approximately every tenth year
since 1G systems were introduced in 1981/1982. Each generation is
characterized by new frequency bands, higher data rates and
non–backward-compatible transmission technology. The first 3G networks
were introduced in 1998 and fourth generation 4G networks in 2008.
4G
4G,
short for fourth generation, is the fourth generation of mobile
telecommunications technology, succeeding 3G. A 4G system must provide
capabilities defined by ITU in IMT Advanced. Potential and current applications
include amended mobile web access, IP telephony, gaming services,
high-definition mobile TV, video conferencing, 3D television, and cloud
computing.
Two 4G
candidate systems are commercially deployed: the Mobile WiMAX standard (first
used in South Korea in 2007), and the first-release Long Term Evolution (LTE)
standard (in Oslo, Norway, and Stockholm, Sweden since 2009). It has however
been debated if these first-release versions should be considered to be 4G or
not, as discussed in the technical definition section below.
In the
United States, Sprint (previously Clearwire) has deployed Mobile WiMAX networks
since 2008, while MetroPCS became the first operator to offer LTE service in
2010. USB wireless modems were among the first devices able to access these
networks, with WiMAX smartphones becoming available during 2010, and LTE
smartphones arriving in 2011. 3G and 4G equipment made for other continents are
not always compatible because of different frequency bands. Mobile WiMAX
is not available for the European market as of April 2012.
HSPA (High Speed Packet Access)
It is an
amalgamation of two mobile protocols, High Speed Downlink Packet Access (HSDPA)
and High Speed Uplink Packet Access (HSUPA), that extends and improves the
performance of existing 3G mobile telecommunication networks using the WCDMA
protocols.
LTE (Long-Term Evolution)
It is a standard
for high-speed wireless communication for mobile devices and data terminals,
based on the GSM/EDGE and UMTS/HSPA technologies. It increases the capacity and
speed using a different radio interface together with core network improvements
WiMAX
WiMAX
(Worldwide Interoperability for Microwave Access) is a family of wireless
communications standards initially designed to provide 30 to 40
megabit-per-second data rates, with the 2011 update providing up to 1
Gbit/s[1] for fixed stations. The name "WiMAX" was created by the
WiMAX Forum, which was formed in June 2001 to promote conformity and
interoperability of the standard. The forum describes WiMAX as "a
standards-based technology enabling the delivery of last mile wireless
broadband access as an alternative to cable and DSL". IEEE 802.16m or WirelessMAN-Advanced is a candidate for the 4G, in
competition with the LTE Advanced standard.
Mobile ID
IMEI International
Mobile Equipment Identity
SEID Secure
Element ID Number (Used for iPay by
Apple)
ICCID Integrated
Circuit Card IDentifier
Core Wireless Networks
GSM (Global System for Mobile
Communications).
GSM is a
standard set developed by European Telecommunications Standards Institute
(ETSI) to describe technologies for second generation (2G) digital cellular
networks. The GSM standard is more improved after the development of third
generation (3G) UMTS standard developed by the 3GPP.
CDMA (Code
Division Multiple Access).
CDMA is
a channel access method used by various radio communication technologies. It
should not be confused with the mobile phone standards called cdma One, CDMA2000 (the 3G evolution of cdmaOne)
and WCDMA (the 3G standard used by GSM carriers), which are often referred to
as simply CDMA, and use CDMA as an underlying channel access method.
TDMA (Time Division Multiple
Access).
TDMA is
a channel access method for shared medium networks. It allows several users to
share the same frequency channel by dividing the signal into different time
slots. The users transmit in rapid succession, one after the other, each using
its own time slot. This allows multiple stations to share the same transmission
medium (e.g. radio frequency channel) while using only a part of its channel
capacity. TDMA is used in the digital 2G cellular systems 2G cellular systems
such as Global System for Mobile Communications (GSM), Personal Digital
Cellular (PDC) and iDEN standard for cellular phones.
EVDO (Evolution-Data Optimized or
Evolution-Data Only).
EVDO is a
telecommunications standard for the wireless transmission of data through radio
signals, typically for broadband Internet access. It uses multiplexing
techniques including code division multiple access (CDMA) as well as time
division multiplexing (TDM) to maximize both individual user's throughput and
the overall system throughput. It has been adopted by many mobile phone service
providers around the world – particularly those previously employing CDMA
networks. EVDO was designed as an evolution of the CDA2000 standard that would
support high data rates and could be deployed alongside a wireless carrier's
voice services.
UMTS (Universal Mobile
Telecommunications System).
UMTS is
a third-generation mobile cellular technology for networks based on the GSM
standard. Developed by the 3GPP (3rd Generation Partnership Project), UMTS is a
component of the International Telecommunication Union IMT-2000 standard set
and compares with the CDMA2000 standard set for networks based on the competing
cdmaOne technology. UMTS employs Wideband Code
Division Multiple Access (W-CDMA) radio access technology to offer greater
spectral efficiency and bandwidth to mobile network operators. UMTS specifies a
complete network system, covering the radio access network (UMTS Terrestrial
Radio Access Network, or UTRAN), the core network (Mobile Application Part, or
MAP) and the authentication of users via SIM cards. The technology described in
UMTS is sometimes also referred to as Freedom of Mobile Multimedia Access
(FOMA) or 3GSM.
HSPA+ or Evolved High-Speed
Packet Access.
HSPA or
HSPA+ is a technical standard for wireless, broadband telecommunication. HSPA+
enhances the widely used WCDMA based 3G networks with higher speeds for the end
user that are comparable to the newer LTE networks. HSPA+ was first defined in
the technical standard 3GPP release 7 and expanded further in later releases.
HSPA+ provides an evolution of High-Speed Packet Access High Speed Packet
Access provides data rates up to 168 Megabits per second (Mbit/s) to the mobile
device and 22 Mbit/s from the mobile device.
Notion in processor, memory, mothercard
Process
This is an isolated memory structure which supports an application in OS hardware and software.
A Windows
Process contains 1 or more Threads.
Thread
This is
a stream of sequential machine-code instructions that the processor executes.
With the exception of Interrupts, any time the CPU runs an Instruction on
behalf of an application, it does so because a thread contained it.
Threads
within a process may access the processes memory (to the extent that the
specific operation on the memory element is "thread-safe" and doesn't
present unreconciled concurrency issues when more than one thread is run
simultaneously).
An
Application may speed its operation by using multiple threads, each performing
an isolated task by running their stream of instructions through a different
CPU Execution unit (CPU/core/virtual core) simultaneously.
Handle
This is
a logical association with a shared resource like a file, Window, memory
location, etc.
When a
thread opens a file, it establishes a "handle" to the file, and
internally it acts like a "name" for that instance of the file.
Handles are used to link to transitory or environmental resources outside the
processes memory structure.
A handle
leak is a type of software issue that can in extreme cases, destabilize a
system.
It is
caused by a program requesting a handle to a resource, and failing to
deallocate it when the program is done with the resource.
An Example : Handles: 48097 Threads: 1602 Processes: 99
Hard disk
Partition table:
The GUID
Partition Table (Globally Unique IDentifier)
is a part of the Unified Extensible Firmware Interface
(UEFI) standard for the layout of the partition table on a physical hard disk.
Many operating systems now support this standard.
SSD (Solid-state drive) disk
|
|
|
SD |
miniSD |
microSD |
|
|
Size |
|
|
|
|
|
Card Type |
SD, SDHC, SDXC |
SD, SDHC |
SD, SDHC, SDXC |
|
Physical |
Area |
768 mm2 (100) |
430 mm2 |
165 mm2 |
|
Card Volume |
1,613 mm3 (100) |
602 mm3 |
165 mm3 |
|
|
Thickness |
2.1 mm |
1.4 mm |
1.0 mm |
|
|
Weight |
Approx. 2g |
Approx. 1g |
Approx. 0.5g |
|
|
Number of pins |
9 pins |
11 pins |
8 pins |
|
|
File System |
FAT16/32 |
FAT16/32 |
FAT16/32 |
|
|
Operating Voltage |
2.7V - 3.6V |
2.7V - 3.6V |
2.7V - 3.6V |
|
|
Write-protect Switch |
YES |
NO |
NO |
|
|
|
Copyright protection |
CPRM |
CPRM |
CPRM |
Bare-board form factors
|
NAND flash is the generic term for the
silicon chips that comprise the actual storage on the SSD. The
"NAND" refers, at a technical level, to the type of logic gates
used in the underlying memory structure. 3 types of NAND: SLC (Single-Level Cell), MLC (Multi-Level Cell, two bits by cell), TLC (Triple-Level Cell, can host eight states and three bits per cell) |
|
|
|
Viking Technology SATA Cube and AMP
SATA Bridge multi-layer SSDs |
|
|
Viking Technology SATADIMM based SSD |
|
|
MO-297 SATA disk-on-a-module (DOM) SSD
form factor |
|
|
A custom-connector SATA SSD |
|
mSATA SSD |
|
|
|
M2 SATA |
|
|
|
PARTITIONS TYPES ----------------------------------------------------
Comparison table between MBR and
GPT. The table highlights the major difference between MBR and GPT.
|
Point of
Comparison |
MBR- Master Boot
Record |
GPT- GUID
Partition Table |
|
Number of Primary Partitions |
4 |
Up to 128 for Windows OS. |
|
Maximum Partition size |
2 TB |
18 exabytes (18 billion gigabytes) |
|
Maximum hard drive size |
2 TB |
18 exabytes (18 billion gigabytes) |
|
Security |
No check sum on data sector |
CRC values are used to ensure data security. Back up GUID
partition table. |
|
Specifications |
BIOS |
UEFI |
|
Partition Name |
Is stored in the partition |
Has a unique GUID and a 36 character name |
|
Multiple boot supported |
Poor support |
Boot loader entries are in different partitions |
|
Operating System Support |
Windows 7 and other older versions like Windows 95/98, Windows
XP etc. |
All major OS like MAC and latest versions of Windows like
Windows 10. |
|
Data recovery |
Data cannot be recovered easily. |
Data can be easily recovered. |
|
Data Corruption |
No way to detect corruption of data. |
Easy to detect |
|
Method of Partition Addressing |
CHS (Cylinder Head Cycle) or LBS (Logical Block Addressing) |
LBA is the only method of addressing partitions. |
|
Size |
512 bytes |
512 bytes per LBA. Each partition entry is 128 bytes. |
|
Partition type code |
1 byte code |
16 byte GUID is used. |
|
Stability |
Less stable as compared to GPT |
Offers more security. |
|
Bootable Version of OS |
Boots 32 bit operating system |
Boots 64 bit operating system |
|
Storage |
Only upto 2TB capacity. Disk size
>2TB is marked as unallocated and cannot be used. |
Disk capacity of 9.44 million TB |
|
Performance |
Lower in performance compared to GPT. |
Offers superior performance if UEFI boot is supported. |
SAN Storage
-------------------------------------------------
Small Form Factor (SFF) SAS and SATA hard
drives
SAS is Serial SCSI, SATA is Serial ATA
SAS drives are generally faster and a little
more expensive than SATA. (SATA are slowly catching up to SAS)
Most SAS controllers will work with SAS and
SATA drives.
SATA controller will work with SATA drives
only.
SFF is 2.5" drives, LFF (Large FF)
3.5" drives
SAS and SATA come in both LFF and SFF. The
servers also have SFF and LFF options for the drive cages.
warranty, 3yr on SAS and 1yr on SATA
SED
Self-encrypting drives (SEDs) encrypt data as
it is written to the disk. Each disk has a disk encryption key (DEK) that is
set at the factory and stored on the disk. The disk uses the DEK to encrypt
data as it writes, and then to decrypt the data as it is read from disk. The
operation of the disk, and its encryption and decryption, is transparent to the
users who are reading and writing data. This default encryption and decryption
mode is referred to as secure erase mode. In secure erase mode, you do not need
an authentication key or password to decrypt and read data. SEDs offer improved
capabilities for an easy and speedy secure erase for situations when disks must
be repurposed or returned for support or warranty reasons.
For the optimal security of the data stored on
the disks, SEDs have a mode referred to as auto-lock mode. In auto-lock mode,
the disk uses an authentication encryption key (AEK) to protect its DEK. When a
disk is powered off, the disks are automatically locked. When the disk is
powered on, the SED requires a valid AEK to read the DEK and unlock the disk to
proceed with read and write operations. If the SED does not receive a valid
authentication key, the data on the disk cannot be read. The auto-lock mode helps
to protect the data when disks are accidentally or intentionally removed from
the system.
In many environments, the secure erase mode may
be sufficient for normal operations and provides you with easy access to
commands that can quickly and securely erase the contents of the disk before a
maintenance or repurposing task. For environments where protection against data
theft is paramount, the auto-lock mode adds an extra layer of access protection
for the data stored on your disks.
ASIC
An application-specific integrated circuit is an integrated circuit (IC) that’s custom-designed for a particular task or application. Unlike FPGA boards that can be programmed to meet a variety of use case requirements after manufacturing, ASIC designs are tailored early in the design process to address specific needs. The two primary ASIC design methods are gate-array and full-custom.
- Gate-array are semi-custom designs that use predefined, diffused layers, transistors, and other active devices to help minimize up-front design work and associated costs.
- Full-custom designs are more complex and more costly, but in return deliver chip flexibility and the ability to process greater workloads.
CABLES ----------------------------------------------------
USB
(Universal Serial Bus) types
|
|
Mini-A (left)
and Mini-B (right) plugs |
|
|
Micro-A plug |
|
|
Micro-B plug |
|
|
USB 3.0 Micro-B
SuperSpeed plug |
|
|
USB 3.0 B type
plug |
|
|
The
USB-C plug |
DVI
(Digital Visual Interface) Types
HDMI
(High-Definition Multimedia Interface) types
DisplayPort

Cable Fibre Optique, Type connector

D-subminiature
The D-subminiature or D-sub is a common type of
electrical connector. They are named for their characteristic D-shaped
metal shield. When they were introduced, D-subs were among the smallest
connectors used on computer systems.
|
Variety |
||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
A male DE-9 connector (plug) |
||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
Male 13W3 connector (plug) |
||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
DA,
DB, DC, DD, and DE sized connectors |
||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
The
DB13W3 connector with three coaxial connections and ten ordinary pins |
||||||||||||||||||||||||||||||||||||||||||||||||||||||
1^ab non-standard shell size |
||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
DA-26 male connector, sometimes incorrectly called DB-26HD or HD-26 |
||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
Comparison of
microminiature D connector and male DE-9 |
||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
D-sub connectors. |
||||||||||||||||||||||||||||||||||||||||||||||||||||||
Electrical Cable-----------------------------------------------------------------------------
|
|
Rallonge
électrique IEC320 C13 vers C14
(mâle-femelle) |
|
|
Câble alimentation
électrique prise anglaise UK mâle
vers embout IEC 320 C13 2m |
|
|
Câble alimentation
électrique prise italienne mâle vers
embout trèfle 2m |
|
|
Câble alimentation
électrique prise italienne mâle vers
embout IEC 320 C13 2m |
|
|
Câble alimentation
électrique prise suisse mâle vers embout
trèfle 2m |
|
|
Adaptateur IEC C14 vers prise électrique CEE7 femelle |
|
|
Adaptateur IEC 320 C14 vers C7 |
|
|
Adaptateur IEC320 C14 vers prise électrique pour IP Power 9258 |
|
|
Cordon d'alimentation en
trèfle (C6) pour ordinateur
portable |
|
|
Câble IEC320 C13 vers C14 (mâle-femelle) pour IP Power 9258 |
|
|
Adaptateur secteur Américain vers Européen |
|
|
Câble alimentation
électrique avec terre 1.80m Schuko vers IEC320 C14 |
|
|
Câble alimentation
électrique 2 pôles IEC320 C8 |
WAN
Cloud computing
Infrastructure
as a Service (IaaS),
Platform
as a Service (PaaS),
Desktop
as a Service (DaaS),
Managed
software as a service (MSaaS),
Mobile
backend as a service (MBaaS),
Information
technology management as a service (ITMaaS).
SDWAN
Software-Defined
Wide-Area Network (SD-WAN or SDWAN):
decoupling
(separating) the networking hardware from its control mechanism
Glossary
Protocols by Open Systems
Interconnection model (OSI) model layer
Layer 1 (Physical Layer)
·
Telephone
network modems
·
IrDA physical layer
·
USB physical layer
·
EIA RS-232, EIA-422, EIA-423, RS-449, RS-485
·
Ethernet physical layer 10BASE-T, 10BASE2, 10BASE5, 100BASE-TX, 100BASE-FX, 1000BASE-T, 1000BASE-SX and
other varieties
·
Varieties
of 802.11 Wi-Fi physical layers
·
DSL
·
ISDN
·
T1 and
other T-carrier links,
and E1 and other E-carrier links
·
ITU Recommendations:
see ITU-T
·
ARINC 818 Avionics
Digital Video Bus
·
CAN bus (controller
area network) physical layer
·
Mobile Industry Processor Interface physical
layer
·
Infrared
·
Frame
Relay
·
FO
Fiber optics
·
X.25
Layer 2 (Data Link Layer)
·
ARCnet Attached
Resource Computer NETwork
·
ARP Address Resolution Protocol
·
ATM Asynchronous Transfer Mode
·
CHAP Challenge
Handshake Authentication Protocol
·
CDP Cisco Discovery Protocol
·
DCAP
Data Link Switching Client Access Protocol
·
Distributed Multi-Link Trunking
·
Distributed Split Multi-Link Trunking
·
DTP Dynamic Trunking Protocol
·
Econet
·
Ethernet
·
FDDI Fiber Distributed Data Interface
·
HDLC High-Level Data Link Control
·
IEEE 802.11 WiFi
·
IEEE 802.16 WiMAX
·
LACP Link Aggregation
Control Protocol
·
L2F Layer 2
Forwarding Protocol
·
L2TP Layer 2 Tunneling Protocol
·
LLDP Link Layer Discovery Protocol
·
LLDP-MED Link
Layer Discovery Protocol - Media Endpoint Discovery
·
MAC Media Access Control
·
Q.710 Simplified Message Transfer Part
·
Multi-link trunking Protocol
·
NDP Neighbor
Discovery Protocol
·
PAgP - Cisco
Systems proprietary link aggregation protocol
·
PPP Point-to-Point Protocol
·
PPTP Point-to-Point Tunneling Protocol
·
PAP Password Authentication Protocol
·
RPR IEEE 802.17 Resilient Packet Ring
·
SLIP Serial Line Internet Protocol
(obsolete)
·
StarLAN
·
Space
Data Link Protocol, one of the norms for Space Data Link from the Consultative Committee for Space Data
Systems
·
STP Spanning Tree Protocol
·
Split multi-link trunking Protocol
·
Token Ring a
protocol developed by IBM; the name can also be used to describe the token passing ring
logical topology that it popularized.
·
Virtual Extended
Network (VEN) a protocol developed by iQuila.
·
VTP VLAN Trunking
Protocol
·
VLAN Virtual Local
Area Network
Network Topology
·
Asynchronous Transfer Mode (ATM)
·
IS-IS, Intermediate System
- Intermediate System (OSI)
·
SPB Shortest Path Bridging
·
MTP Message Transfer Part
·
NSP Network Service
Part
Layer 2.5[edit]
·
ARP Address Resolution Protocol
·
MPLS Multiprotocol Label Switching
·
PPPoE Point-to-Point
Protocol over Ethernet
·
TIPC Transparent
Inter-process Communication
Layer 3 (Network Layer)
·
CLNP Connectionless
Networking Protocol
·
IPX Internetwork
Packet Exchange
·
NAT Network Address Translation
·
SCCP Signalling
Connection Control Part
·
AppleTalk
DDP
·
HSRP Hot Standby Router protocol
·
VRRP Virtual Router
Redundancy Protocol
·
IP Internet
Protocol
·
ICMP Internet Control
Message Protocol
·
ARP Address Resolution Protocol
·
RIP Routing Information Protocol (v1 and
v2)
·
OSPF Open Shortest Path First (v1 and v2)
·
IPSEC IPsec
Layer 3+4 (Protocol Suites)
·
DECnet
·
IPX/SPX
Layer 4 (Transport Layer)
·
AEP AppleTalk Echo Protocol
·
AH Authentication Header over IP or IPSec
·
DCCP Datagram
Congestion Control Protocol
·
ESP Encapsulating Security Payload
over IP or IPSec
·
FCP Fibre Channel Protocol
·
NetBIOS NetBIOS, File Sharing and Name Resolution
·
IL Originally
developed as transport layer for 9P
·
iSCSI Internet Small
Computer System Interface
·
NBF NetBIOS
Frames protocol
·
SCTP Stream Control
Transmission Protocol
·
Sinec H1 for telecontrol
·
TUP, Telephone User Part
·
SPX Sequenced
Packet Exchange
·
NBP Name Binding Protocol {for AppleTalk}
·
TCP Transmission Control Protocol
·
UDP User Datagram Protocol
·
QUIC
Layer 5 (Session Layer)
This
layer, presentation Layer and application layer are combined in TCP/IP model.
·
9P Distributed
file system protocol developed originally as part of Plan 9
·
ADSP
AppleTalk Data Stream Protocol
·
ASP
AppleTalk Session Protocol
·
H.245 Call Control
Protocol for Multimedia Communications
·
iSNS Internet
Storage Name Service
·
NetBIOS,
File Sharing and Name Resolution protocol - the basis of file sharing with
Windows.
·
NetBEUI,
NetBIOS Enhanced User Interface
·
NCP NetWare Core Protocol
·
PAP Printer
Access Protocol
·
RPC Remote Procedure Call
·
RTCP RTP Control Protocol
·
SDP Sockets Direct Protocol
·
SMB Server Message Block
·
SMPP Short Message Peer-to-Peer
·
SOCKS "SOCKetS"
·
ZIP Zone Information Protocol {For
AppleTalk}
·
This layer
provides session management capabilities between hosts. For example, if some
host needs a password verification for access and if credentials are provided
then for that session password verification does not happen again. This layer
can assist in synchronization, dialog control and critical operation management
(e.g., an online bank transaction).
Layer 6 (Presentation Layer)
·
TLS Transport Layer Security
·
AFP Apple Filing Protocol
·
Independent
Computing Architecture (ICA), the Citrix system core protocol
·
Lightweight
Presentation Protocol (LPP)
·
NetWare
Core Protocol (NCP)
·
Network
Data Representation (NDR)
·
Tox,
The Tox protocol is sometimes regarded as part of both the presentation and
application layer
·
eXternal Data Representation (XDR)
·
X.25 Packet
Assembler/Disassembler Protocol (PAD)
Layer 7 (Application
Layer)
·
SOAP, Simple Object Access Protocol
·
Simple Service Discovery Protocol,
A discovery protocol employed by UPnP
·
TCAP, Transaction
Capabilities Application Part
·
DHCP
·
DNS Domain Name
System
·
BOOTP Bootstrap
Protocol
·
HTTP
·
HTTPS
·
NFS
·
POP3
·
SMTP
·
SNMP
·
FTP
·
NTP
·
IRC
·
Telnet
·
SSH
·
TFTP
·
IMAP
·
Gemini
-------- End of OSI Model
------------------------------------------------
Which .NET Framework versions are
installed
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\NET
Framework Setup\NDP\v4\Full.
.NET Framework 4.5............... 378389
.NET Framework 4.5.1............ 378675
.NET Framework 4.5.2............ 379893
.NET Framework 4.6............... 393295
.NET Framework 4.6.1............ 394254
.NET Framework 4.6.2............ 394802
.NET Framework 4.7............... 460798
.NET Framework 4.7.1............ 461308
.NET Framework 4.7.2............ 461808
.NET Framework 4.8............... 528040
Remote control in Power out
RMM2 (Remote Management 2), Intel
DRAC (Dell Remote Access Control), Dell
ILOM (Integrated Lights Out Manager), Oracle
(old Sun)
IMM (Integrated Management
Module), IBM
ILO (Integrated
Lights-Out), HP
----- end of document -----------------------